Get in touch
580-749-6060
info (at) abtok.com
Secure Your Most Valuable Asset.
Your Business.
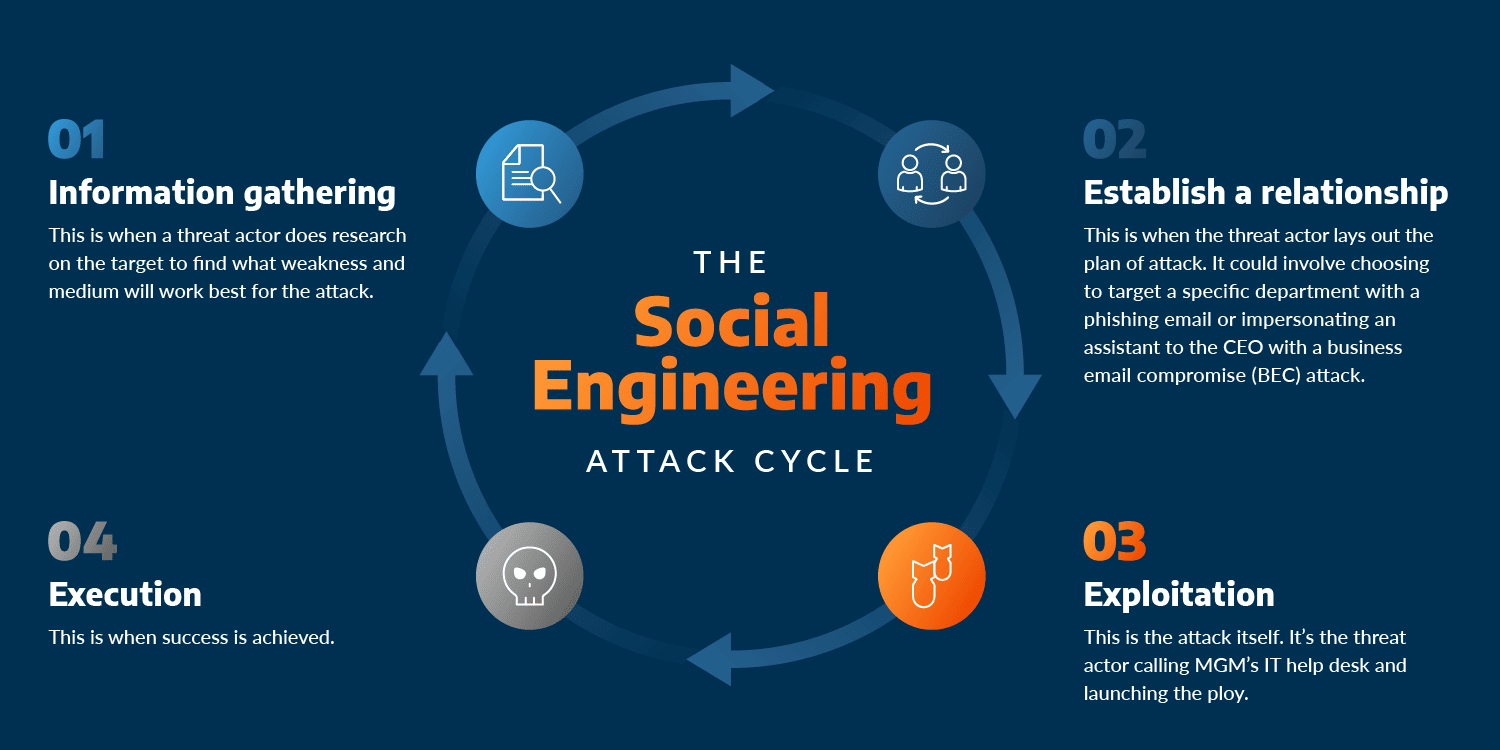
March 21, 2025
Hackers are now exploiting a social engineering tactic called “ClickFix” to trick users into downloading malware right onto their machine. These fake alerts appear credible and convince users to bypass security measures, putting your accounts and data at serious risk. If you are a current customer and we provide you with cybersecurity services: We’re actively improving your security defenses and looking for any indication of attack in your network. We also want to take this time to educate your team to recognize these fake alerts. If you receive a suspicious message urging you to “fix” your account or system, please contact us before taking action. below is an example of what you might see on your screen in this kind of attack. If you are not an ABT Solutions customer or do not purchase cybersecurity from us, here’s how we can help: Our team can help implement enhanced security measures, provide user awareness training, and ensure your team can recognize these increasingly convincing social engineering attacks. I’d like you to click the link below to receive a free vulnerability assessment showing how we can improve your security and reduce the risk of social engineering attacks like ClickFix . Here is a link to schedule a vulnerability risk assessment: Click Here Let’s work together to ensure your organization is protected from this rising threat. Dedicated to keeping you secure, Braden A. Lampe

September 24, 2024
2024's Biggest Data Breaches and What They Mean for Your Business Data breaches are always lurking as a potential threat, and when they happen, the fallout can be devastating for your business and customers. In today’s post, we’re taking a look at some of the biggest breaches of 2024 to put the growing cybersecurity concern into perspective. According to Cybersecurity Magazine , the total cost of cybercrime is projected to hit a staggering $9 trillion in 2024 and climb to over $10 trillion in 2025. To put that in context, that’s more than the GDP of almost every country in the world—except for two. It’s safe to say cybersecurity is not something you want to take lightly. Before diving into the list, it’s worth mentioning that 2024 also saw the most expensive tech outage in history. A CrowdStrike update that affected Microsoft systems ended up costing companies over $5 billion . While this wasn’t a data breach, it’s a powerful reminder of how damaging tech issues can be. Now, let’s get into the biggest data breaches of 2024. National Public Data Breach — 2.7 Billion Records This one’s a monster. Just a few weeks ago, a hacking group claimed to have stolen 2.7 billion personal records —including the information of virtually every person in the U.S., Canada, and the U.K. The stolen data includes social security numbers, and while experts are still verifying how accurate and complete the breach is, it’s safe to assume most of this sensitive data has been compromised. The good news? Well, we’re all in the same boat. Everyone will need to keep a close eye on their accounts and credit, and freezing your credit is a great step toward protecting your identity. It’s also a good idea to get in the habit of unfreezing it only when applying for loans or credit cards. Ticketmaster — 560 Million Records In April and May of 2024, cybercriminals gained access to Ticketmaster’s database , exposing the personal and financial details of 560 million customers . The breach revealed names, emails, phone numbers, and payment info. The fallout was immediate, with customers reporting identity theft and unauthorized transactions. On top of that, this breach came right before the U.S. Justice Department sued Ticketmaster’s parent company, Live Nation, for anti-competitive behavior. Tough year for them. Change Healthcare — 145 Million Records In February 2024, Change Healthcare was hit by a major ransomware attack, compromising 145 million records . This breach exposed personal info, including names, addresses, social security numbers, and medical records. Given the sensitive nature of healthcare data, this was one of the largest and most damaging breaches in history. It has forced healthcare providers and insurers to rethink their security strategies moving forward. Dell — 49 Million Records In May 2024, Dell became the victim of a brute force attack when a hacker gained access through one of their resellers' portals. This breach exposed the data of 49 million customers, including names, emails, payment info, and account details. Dell has faced heavy criticism and is working to improve their cybersecurity protocols in response to the breach, while regulators are watching closely. AT&T — 73 Million Records AT&T suffered a significant breach in March 2024, affecting 73 million customers . This breach exposed personal information like social security numbers, account details, and passcodes. What makes this even worse is that the data had been compromised since 2019 . AT&T is now facing potential class action lawsuits as they work to contain the damage and protect their current customers. Why This Matters for You You might not have millions of customers like these giants, but that doesn’t mean you’re safe from cyberattacks. Businesses of all sizes are vulnerable. The key is to get ahead of the threat by implementing strong security measures. That includes training your team on password best practices, educating them about phishing attacks, and making sure you have a cybersecurity strategy in place. At ABT Solutions, we specialize in keeping businesses like yours safe from cyber threats. Want to learn more about how we can help? Give us a call today or Click Here to receive a free cybersecurity risk assessment!

September 18, 2024
Your Team Could Be Your Biggest Cybersecurity Risk—Or Your Strongest Defense When it comes to your business’ cybersecurity, one vulnerability stands out above the rest. This one can either cripple your organization or, if handled correctly, become one of your greatest assets. What’s this vulnerability? Your team. Human error is one of the easiest ways for hackers to slip through your defenses, but with the right training and mindset, your employees can become a strong line of defense. Let’s talk about how you can encourage your team to adopt cybersecurity best practices both at work and at home, reducing the chance of phishing and other cyber threats. These recommendations are based on guidance from the Cybersecurity and Infrastructure Security Agency (CISA). While they’re designed for home users, they’re equally valuable in the workplace. How Your Team Can Strengthen Your Cybersecurity They Know How to Spot Phishing Scams Phishing remains one of the most common and dangerous cybersecurity threats. These scams trick employees into sharing sensitive information or granting access to resources that should stay locked down. It only takes one successful phishing attack to open the door to larger breaches or even a full-scale cyberattack. But if your team is trained to recognize phishing attempts and knows how to respond when they encounter one, they’re far less likely to fall for these tricks. Make sure everyone is up to date on your company’s protocols for handling suspected phishing emails and other threats. They Use Strong, Unique Passwords We all know the temptation to reuse passwords across accounts or to create simple, easy-to-remember credentials. But let’s be clear: this is unacceptable. Your team needs to understand that strong, unique passwords are a non-negotiable part of your security strategy. Password management software can help simplify the process, ensuring that your employees don’t take shortcuts when it comes to protecting their accounts. They Use Multi-Factor Authentication (MFA) Think of multi-factor authentication (MFA) as adding an extra lock to your data. It enhances security by requiring an additional verification step, such as a code from an app or a fingerprint scan, on top of the usual username and password. By implementing MFA wherever possible, you make it significantly harder for unauthorized users to access your data, even if they somehow get hold of a password. It’s a simple but effective way to boost security across the board. They Keep Software Updated We all know software updates can be a pain, but they’re critical for security. Most updates address vulnerabilities and close security gaps that cybercriminals might otherwise exploit. Plus, updates often improve performance, helping your business stay productive. While keeping software up-to-date is mainly your IT team’s responsibility, it helps if your employees understand the importance of these updates. The more they appreciate why updates matter, the fewer headaches you’ll face in the long run. We’re Here to Help Keep Your Business Secure At ABT Solutions, we’re dedicated to helping businesses like yours implement practical cybersecurity measures and providing the training your team needs to stay vigilant. Ready to take your security to the next level? Give us a call today or Click Here to receive a free cybersecurity risk assessment.

August 20, 2024
In today's digital age, email remains a vital tool for communication. However, its convenience can also make it a risky medium, especially when it comes to sharing sensitive information. Whether it's personal data, financial details, or confidential business documents, sending unencrypted emails can expose you to significant security threats. Here’s why you should never send sensitive information through email without encryption and how we can help secure your communications. The Risks of Unencrypted Emails Interception by Hackers: Unencrypted emails are like postcards—they can be intercepted and read by anyone during transmission. Cybercriminals often target emails to steal sensitive information, leading to identity theft, financial loss, or worse. Without encryption, your data is left vulnerable to these malicious actors. Data Breaches: Organizations are increasingly becoming targets of data breaches, where massive amounts of sensitive information are exposed. If your unencrypted email is caught up in a breach, it could lead to severe consequences, including legal ramifications and damage to your reputation. Lack of Privacy: Unencrypted emails can be accessed not only by hackers but also by unauthorized individuals within your organization or email service providers. This lack of privacy can result in confidential information being misused or shared without your consent. Compliance Violations: Many industries are governed by strict regulations regarding the handling of sensitive information. Sending unencrypted emails can result in non-compliance with laws like GDPR, HIPAA, or PCI-DSS, leading to hefty fines and legal actions against your business. The Importance of Email Encryption Email encryption is the process of converting your message into an unreadable format that can only be deciphered by the intended recipient. It ensures that even if your email is intercepted, the contents remain protected and inaccessible to unauthorized parties. Protect Your Data: Encryption safeguards your information, ensuring that only authorized recipients can access it. Maintain Compliance: By using encryption, you stay compliant with industry regulations, avoiding costly penalties. Build Trust: Securing your emails demonstrates your commitment to protecting your clients' information, helping to build trust and confidence in your business. How We Can Help At ABT Solutions, we offer robust email encryption services tailored to meet your security needs. Our solutions are designed to seamlessly integrate with your existing email platform, providing end-to-end encryption without complicating your workflow. By partnering with us, you can ensure that your sensitive information remains confidential and secure, no matter where it’s sent.

By b328cabadd620e9eeb96502345549129_cc_2214
•
August 13, 2024
The Growing Importance of Third-Party Assessments in Cybersecurity In today’s rapidly evolving digital landscape, cybersecurity has become a critical concern for businesses of all sizes. The threat of cyberattacks is ever-present, and the consequences of a breach can be devastating. As organizations strive to protect their sensitive data and maintain customer trust, many are turning to third-party assessments to ensure their security measures are up to par. In fact, insurance companies are now increasingly requiring these assessments as a prerequisite for coverage. But why are third-party assessments so important, and what can they do for your business? Why Third-Party Assessments Matter Objective Evaluation: A third-party assessment provides an objective evaluation of your current security posture. Unlike internal audits, which can be influenced by biases or a lack of comprehensive knowledge, a third-party brings a fresh, unbiased perspective. This ensures that any vulnerabilities or weaknesses are identified accurately and addressed effectively. Meeting Insurance Requirements: Cyber insurance is becoming a crucial part of business risk management, offering protection against the financial fallout of a cyberattack. However, insurance companies are tightening their requirements, with many now mandating third-party assessments as a condition for coverage. These assessments help insurers gauge your level of risk, ensuring that you meet the necessary criteria to qualify for coverage and potentially lowering your premiums. Staying Ahead of Threats: Cyber threats are constantly evolving, with new vulnerabilities emerging daily. A third-party assessment helps you stay ahead of these threats by providing up-to-date insights into the latest risks and how they apply to your specific environment. This proactive approach allows you to implement the necessary defenses before an attack occurs. Building Customer Trust: Customers are increasingly aware of the risks associated with data breaches and expect the businesses they interact with to prioritize cybersecurity. By undergoing a third-party assessment, you demonstrate your commitment to protecting their information, which can significantly boost their confidence in your brand. Regulatory Compliance: Many industries are subject to strict regulatory requirements concerning data protection. A third-party assessment can help ensure that your business remains compliant with these regulations, avoiding costly fines and legal issues. It also provides documentation that can be used to prove compliance to regulators, auditors, and other stakeholders. Guidance on Best Practices: Third-party assessors are typically experts in the field of cybersecurity, with a deep understanding of industry best practices. They can provide valuable guidance on how to improve your security measures, from implementing advanced technologies to refining your internal processes. This expert advice can be instrumental in elevating your security posture and reducing your risk of a breach. The Role of Insurance in Cybersecurity As cyber insurance becomes more prevalent, insurers are placing greater emphasis on ensuring that their clients are taking adequate precautions to protect themselves. This shift is driven by the increasing frequency and severity of cyberattacks, which have led to significant payouts by insurance companies. To mitigate their risk, insurers are now requiring businesses to undergo third-party assessments as part of the underwriting process. These assessments provide insurers with a clearer picture of your organization’s risk level, allowing them to offer tailored coverage that reflects your specific needs. Moreover, businesses that invest in third-party assessments and demonstrate a strong security posture may benefit from lower premiums and better coverage terms. Don’t Wait Until It’s Too Late The reality is that no organization is immune to cyber threats. Whether you’re a small business or a large enterprise, the risk of a cyberattack is real—and the consequences can be severe. By investing in a third-party assessment, you’re taking a crucial step in protecting your business, meeting insurance requirements, and building a stronger, more resilient security posture. Take Action Now If your business hasn’t undergone a third-party cybersecurity assessment, now is the time to act. Not only will it help you meet the evolving requirements of your cyber insurance policy, but it will also provide peace of mind knowing that your organization is better protected against the ever-growing threat of cyberattacks. How We Can Help At ABT Solutions, we specialize in providing comprehensive third-party assessments that are tailored to your business's unique needs. Our team of experts will thoroughly evaluate your security posture, identify vulnerabilities, and offer actionable recommendations to strengthen your defenses. Whether you’re looking to meet insurance requirements, achieve regulatory compliance, or simply enhance your cybersecurity, we’re here to help. Contact us today to schedule your assessment and take the first step toward a more secure future.

By b328cabadd620e9eeb96502345549129_cc_2214
•
August 6, 2024
As a savvy business owner and Microsoft Windows user, you always update your browser and only visit secure websites. But do your employees exercise the same level of caution? If not, your data could be at serious risk. This is especially true now that hackers are using clever techniques to trick Windows users into opening malicious websites in unique ways. What Is Malware and How Does It Usually Spread? Malware is software that cybercriminals use to jeopardize company devices, from cell phones to desktops. While some online threats originate from competing companies that want to drive another business by destroying customer trust or locking them out of their account, others steal data, funds, and identities. Whatever the reason behind an attack, malware comes in many different types. For instance, viruses and worms make copies of themselves to infect one computer or multiple in a network, respectively. Others, like adware and Trojan horses, pretend to be something they’re not, so employees let down their guard and interact with them. Malware also spreads in unique ways, such as when downloading faux software or legitimate programs that hackers have tampered with. Clicking suspicious links in emails and on websites also causes malware to spread. Since January 2023, this has become a major cause for concern. Check Point Research (CPR) has announced that hackers use clever techniques to trick Windows users into opening malicious websites. Window’s New Zero-Day Flaw Check Point Research said a new malware campaign surfaced in January 2023. In it, hackers use .URL files that act as shortcuts to lure Windows users to affected website pages. These shortcuts appear in .PDF book files and may seem innocuous, but nothing could be further from the truth. Suppose you or one of your employees click on the file. In that case, it opens an outdated version of Internet Explorer with many zero-day flaws. While updated versions have patches for these issues, older ones remain vulnerable, making them perfect for phishing and other cyberattacks. The browser leads users to a faux website page where hackers can deploy malware and steal information. Microsoft’s Remediation of This Flaw During July Patch Tuesday, researchers at CPR explained that hackers are using clever techniques to trick Windows users into opening malicious websites, then using exploit kits and info-stealers to grab credentials and financial data. While it’s one of the biggest Windows threats in recent months, it’s far from the only one. Another flaw, CVE-2024-38080, grants attackers Microsoft virtual machine hypervisor privileges. Microsoft now has patches available for these two active flaws alongside 140 others. If you want to reduce your chances of falling victim to social engineering, especially in cases where hackers are using clever techniques to trick Windows users into opening malicious websites, be sure to keep your browser and your Windows machine updated. How We Can Help At ABT Solutions, we understand the critical importance of keeping your software and systems up to date to protect your business from evolving cyber threats. Our comprehensive IT services include proactive monitoring and regular updates to ensure that your Windows machines, browsers, and other software are always running the latest security patches. We also offer employee training to help your team recognize and avoid the latest social engineering tactics that hackers use. Don’t leave your business vulnerable—partner with us to safeguard your data and maintain a secure, resilient IT environment. Contact us today to learn more about how we can help protect your organization from the latest threats.

By b328cabadd620e9eeb96502345549129_cc_2214
•
July 31, 2024
Potential data breaches pose a growing threat to organizations, with phishing attacks being the most prevalent method hackers use to steal sensitive information. It has become one of the most widespread online dangers, and understanding how it works is crucial to protecting your users. Let's go into what phishing attacks are and explore some best practices to safeguard your network. What is a Phishing Attack? Phishing is a deceptive tactic where scammers attempt to trick you into revealing confidential information by masquerading as a trustworthy entity. This often involves misleading emails, messages, or websites that appear to be from reliable sources such as banks or well-known companies. The aim is to phish for information like passwords or financial details, which can then be exploited for identity theft, fraud, and malware deployment. Four Practices to Help Protect Your Network Here are some strategies to prevent phishing attacks from compromising your network: Exercise caution with links and attachments - Avoid clicking on links or downloading attachments from unfamiliar or suspicious sources. Phishing emails often contain links that appear legitimate but lead to malicious sites. Always hover over a link to verify the URL before clicking. Verify the sender’s identity - Carefully check the sender's email address, especially if the message is unexpected or requests sensitive information. Phishers often use email addresses that closely resemble legitimate ones, with subtle differences. Be alert to phishing signs - Watch out for generic greetings, spelling or grammar errors, and urgent requests for personal or financial information. Reputable companies typically address you by name and do not pressure you to take immediate action. Enable Multi-Factor Authentication - Activate MFA wherever possible to add an extra layer of security. Even if a phisher obtains your password, MFA can significantly reduce or prevent unauthorized access. Understanding phishing, and taking proactive steps to defend against it, are essential for protecting your business. Implementing comprehensive training, including simulated phishing exercises, can raise awareness among employees who may not naturally prioritize security. How We Can Help Protect Your Organization At ABT Solutions, we are committed to safeguarding your organization from the growing threat of phishing attacks and other cyber threats. Our comprehensive cybersecurity services include advanced email security solutions, regular network monitoring, and multi-factor authentication implementation to provide robust protection for your sensitive information. We also offer tailored employee training programs, including simulated phishing exercises, to ensure your team is well-prepared to recognize and respond to phishing attempts. Don’t leave your organization vulnerable—partner with us to create a secure, resilient defense against cyberattacks. Contact us today to learn how we can help protect your business from the dangers of phishing and other online threats.
LINKS
STAY INFORMED ABOUT EMERGING THREATS!
Contact Us
Awesome! You will be added to our Threat Intelligence Email Alerts.
Oops, there was an error. Please try again later.
© 2025
All Rights Reserved | ABT Solutions, LLC

